How hackers try to break into Windows — a new scam campaign
Cybersecurity researchers at Trustwave SpiderLabs have uncovered a clever cybercrime campaign that attacks Windows. Hackers then use the Windows search function and trick victims into downloading malware.
Experts say the campaign is small-scale and smart at the same time.
"The technique cleverly masks the attacker's true intent and exploits the user's trust in familiar interfaces and frequently repeated actions, such as opening links in email attachments," the researchers wrote .
How is a cyber attack carried out?
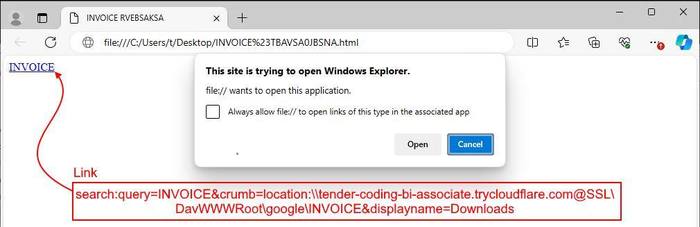
The attack starts with a phishing email that looks like an invoice or similar document. It carries a compressed .ZIP file that contains an HTML file. Mail so successfully bypasses antivirus and mail protection programs that pay little attention to compressed files.
Photo: Trustwave
The HTML file then opens the browser and makes it interact directly with Windows Explorer's search function. In response, Windows Explorer looks for items marked as "INVOICES" in a special directory — a server accessed from Cloudflare. In addition, the search function is renamed to "Downloads". This way the user is fooled into looking at a "downloaded" file and not a .ZIP archive.
Photo: Trustwave
In addition to these files, the user will also be presented with a .LNK document; It points to a batch .BAT scenario that exists on the same server. If this scenario is activated, other malicious operations are started.
When the experts started to study the campaign, the server was already closed. Consequently, the researchers were unable to detect the malware.
How to protect yourself from such a cyber attack
To protect against such threats, we can turn off the function (so-called search-ms/search URI protocol coaches) from the computer settings, which allows programs to search for files in the system in a specific way. To do this, you need to enter the settings of the computer and make changes to the Windows registry - the database in which the configuration information of the programs is stored.
Also, be wary of emails with links attached to:
"Consumers must navigate an increasingly complex threat environment, so continuous education and proactive defense strategies are critical to protect against such deceptive tactics," the researchers said .
If you're interested in cybersecurity and want to better protect yourself in the digital world, check out our other articles here .